Silent Push
Real-time DNS, domain, and infrastructure threat intel.
A Word from the CyberLion
Main Features
Proactive Detection
Identify threats before attacks using IOFA™ intelligence
Global Infrastructure Mapping
Daily scans of global IPv4/IPv6 space revealing relationships
Behavioral Fingerprinting
Generate unique behavioral fingerprints of attacker TTPs
One-Click Pivoting
Traverse attacker infrastructure without complex manual lookups
First-Party Data
Complete data independence with timely, accurate intelligence sourcing
Product Suite
Silent Push Platform
Comprehensive threat hunting and intelligence platform designed to track pre-weaponized infrastructure with behavioral fingerprints and IOFA™ feeds
Community Edition
Free threat hunting and cyber defense tool featuring basic and advanced DNS queries for security teams and researchers
IOFA™ Feed Scanner
Enhanced threat intelligence management module enabling seamless access to enriched feed data with automated detection workflows and export capabilities
Live Scan
Real-time URL analysis tool extracting data across 100+ categories including HTML, screenshots, SSL data, and risk scores from any URL
Trusted by Leading Companies






Use Cases & News
Silent Push has been accepted on the Tradewinds Solutions Marketplace, providing streamlined access to its platform and services for the Department of Defense and other government agencies seeking advanced threat…
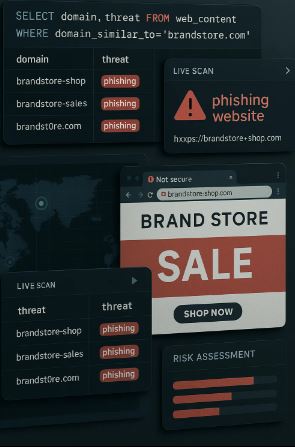
Organizations face increasing threats from sophisticated impersonation campaigns targeting their digital brand presence. Recent research has identified thousands of fake storefronts operated by organized criminal groups, targeting major retailers through…
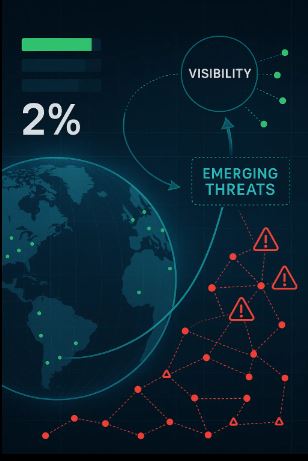
Security teams face a critical challenge where only about 2% of threat actor infrastructure is actively tracked, leaving significant blind spots in their defense posture. Silent Push addresses this gap…