Outpost24
Visibility is Nothing without Context
A Word from the CyberLion
Main Features
Continuous Visibility – 24/7/365
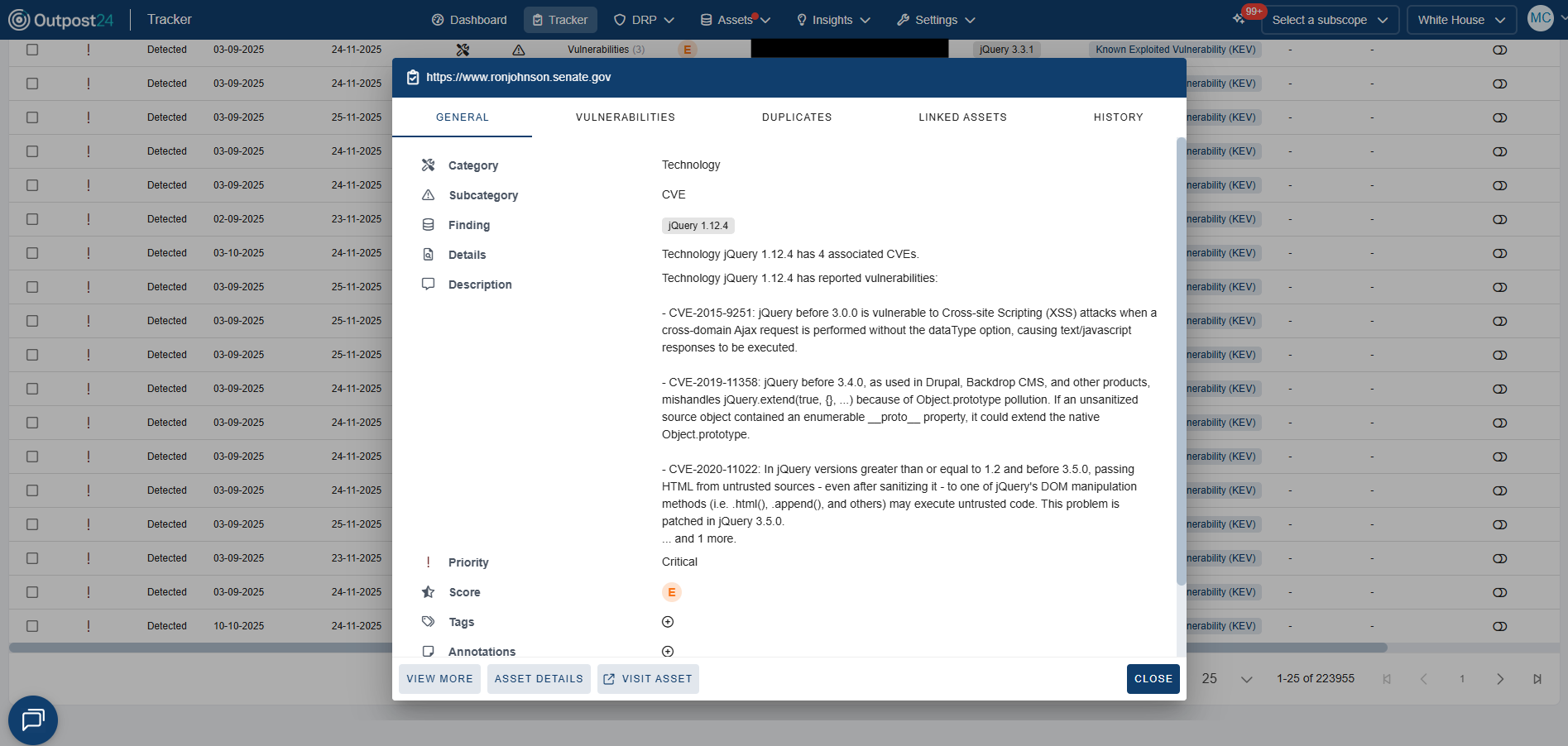
Automatically discover all known and unknown internet-facing assets, uncovering relationships across domains, subdomains, IPs, cloud instances, third-party integrations, and partner connections. Identify and mitigate threats proactively, before they become incidents.
A Single Source of Truth
Integrate asset, vulnerability, and risk data into your SIEM, CMDB, or SOAR tools. Sync with ServiceNow or Splunk to streamline workflows and maintain a single source of truth.
Customizable Alert Workflows
Get real-time alerts that integrate with your tech stack and automate next steps for a faster, smoother remediation process.
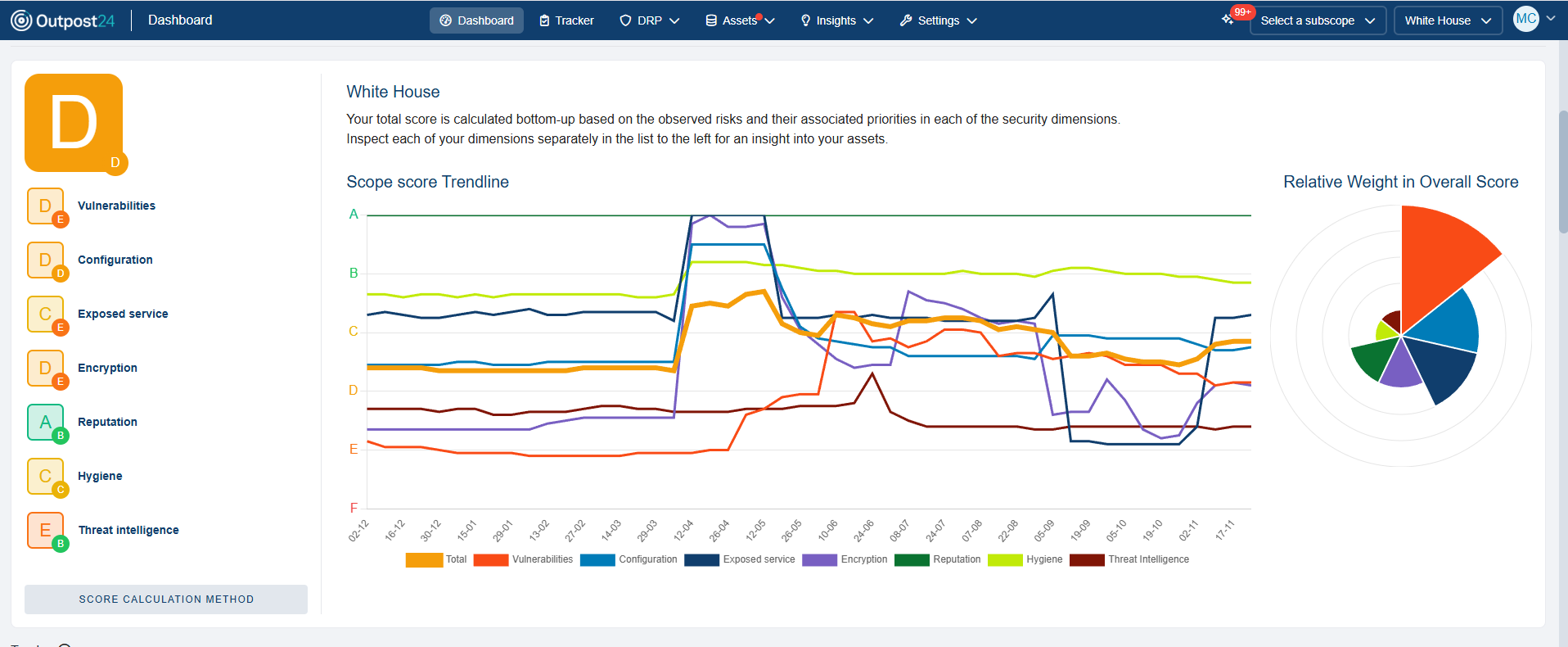
Benchmark and Track Your Security Posture
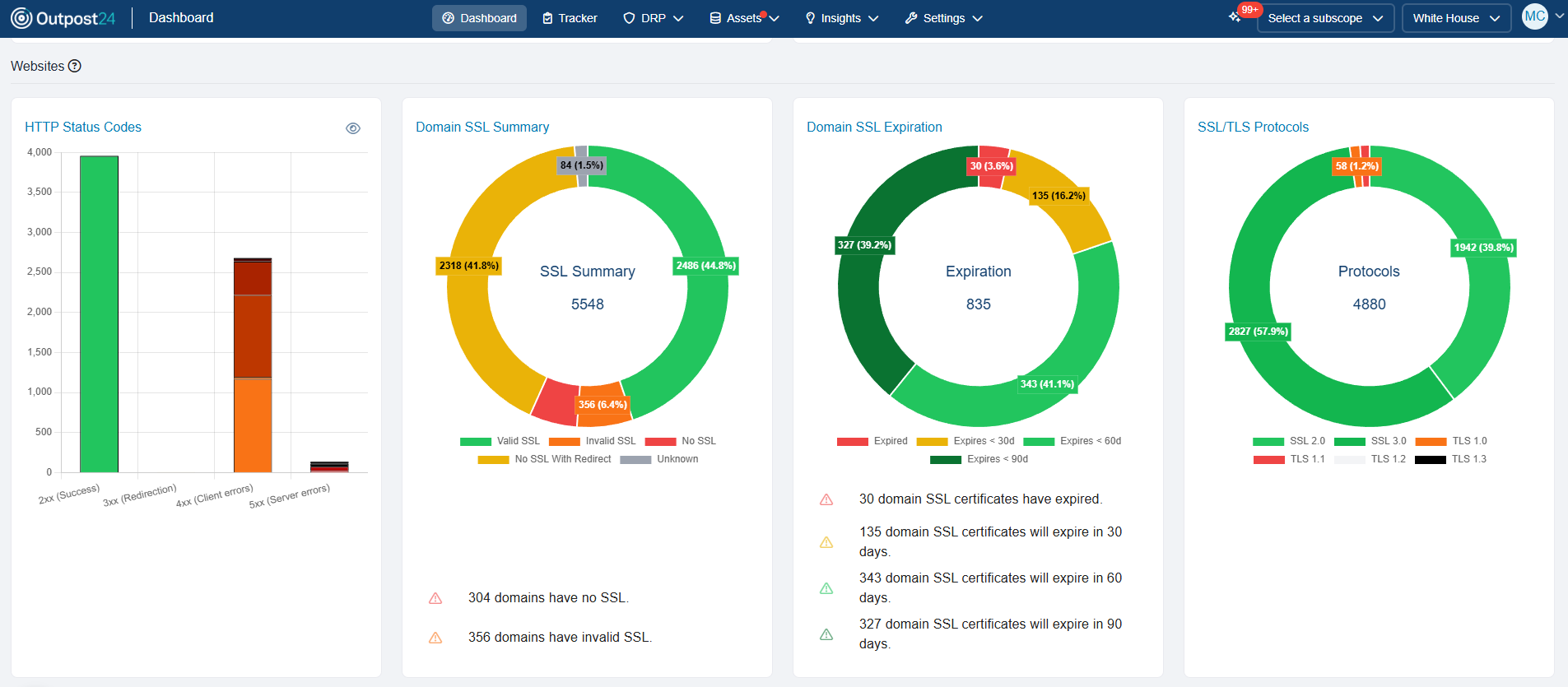
Get unique attack surface scoring and historical trends across your entire scope, at both the asset and observation level, along with industry benchmarks.
Keeping 3000+ Organizations Safe
Product Suite
Outpost24 EASM
Get automatic, comprehensive discovery of both known and unknown internet-facing assets and their vulnerabilities with Outpost24’s EASM Platform.
Outpost24 CompassDRP
Get visibility into both public-facing internal assets and external threats across the open, deep, and dark web in a single cloud-based solution.
Outpost24 CyberFlex
Combine the power of Outpost24’s EASM solution with our certified penetration testing experts and PTaaS to discover, test, and validate both known and unknown applications.
Trusted by Leading Companies





Use Cases & News
Web applications, mobile apps, and APIs are among the most targeted components in modern IT environments. Attackers constantly probe for weaknesses that could expose sensitive data, disrupt services, or damage…
In a world where digital footprints expand every day, organizations face not just traditional threats inside the network but also evolving dangers lurking outside where attackers look first. Two key…
In today’s digital landscape, your organization’s external attack surface—all the publicly exposed systems, domains, cloud services, APIs and other internet-facing assets—grows faster than most teams can track manually. Every forgotten…