AccuKnox
Zero Trust Cloud Security. From Code to Runtime.
A Word from the CyberLion
Main Features
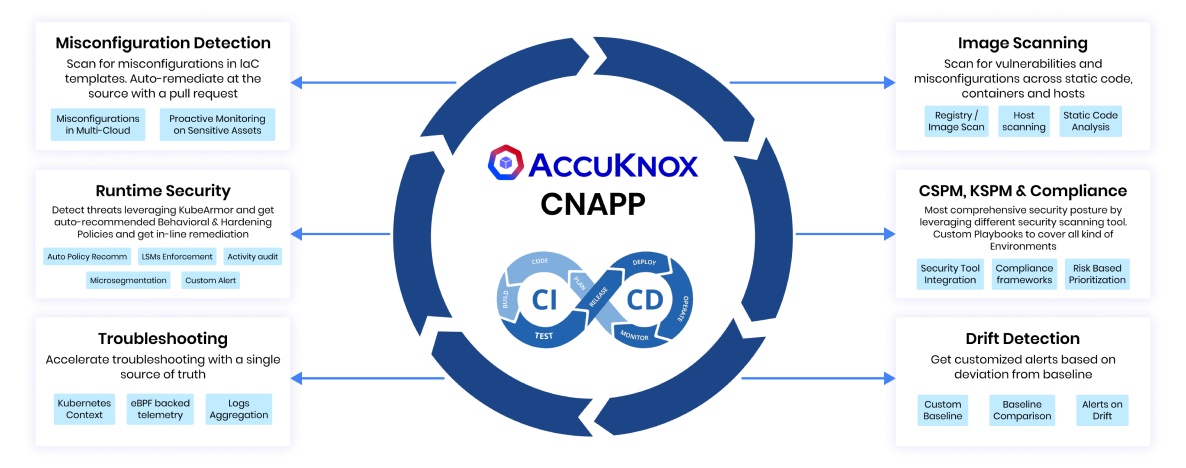
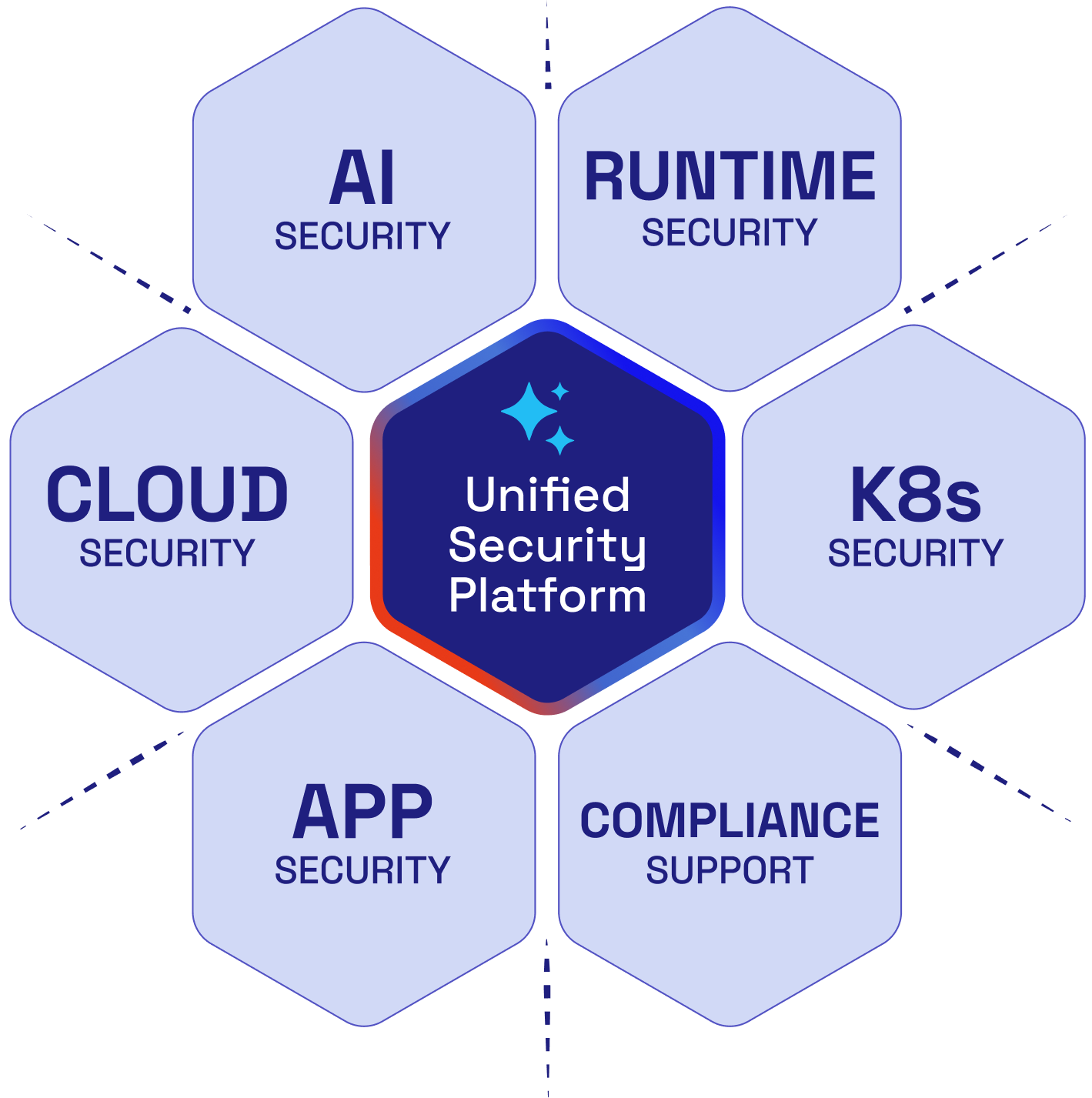
Unified Security Platform
combines CSPM, CWPP, KSPM, and API Security in a single pane of glass.
Zero Trust by Design
continuous verification across workloads, users, and data flows.
Runtime Protection
advanced behavioral analytics, anomaly detection, and micro-segmentation.
AI & LLM Security
protect data pipelines, models, and GPU environments used in AI and machine-learning workflows.
Recognized Leader
rated 4.6 / 5 stars on Gartner Peer Insights for Cloud-Native Security.
Product Suite
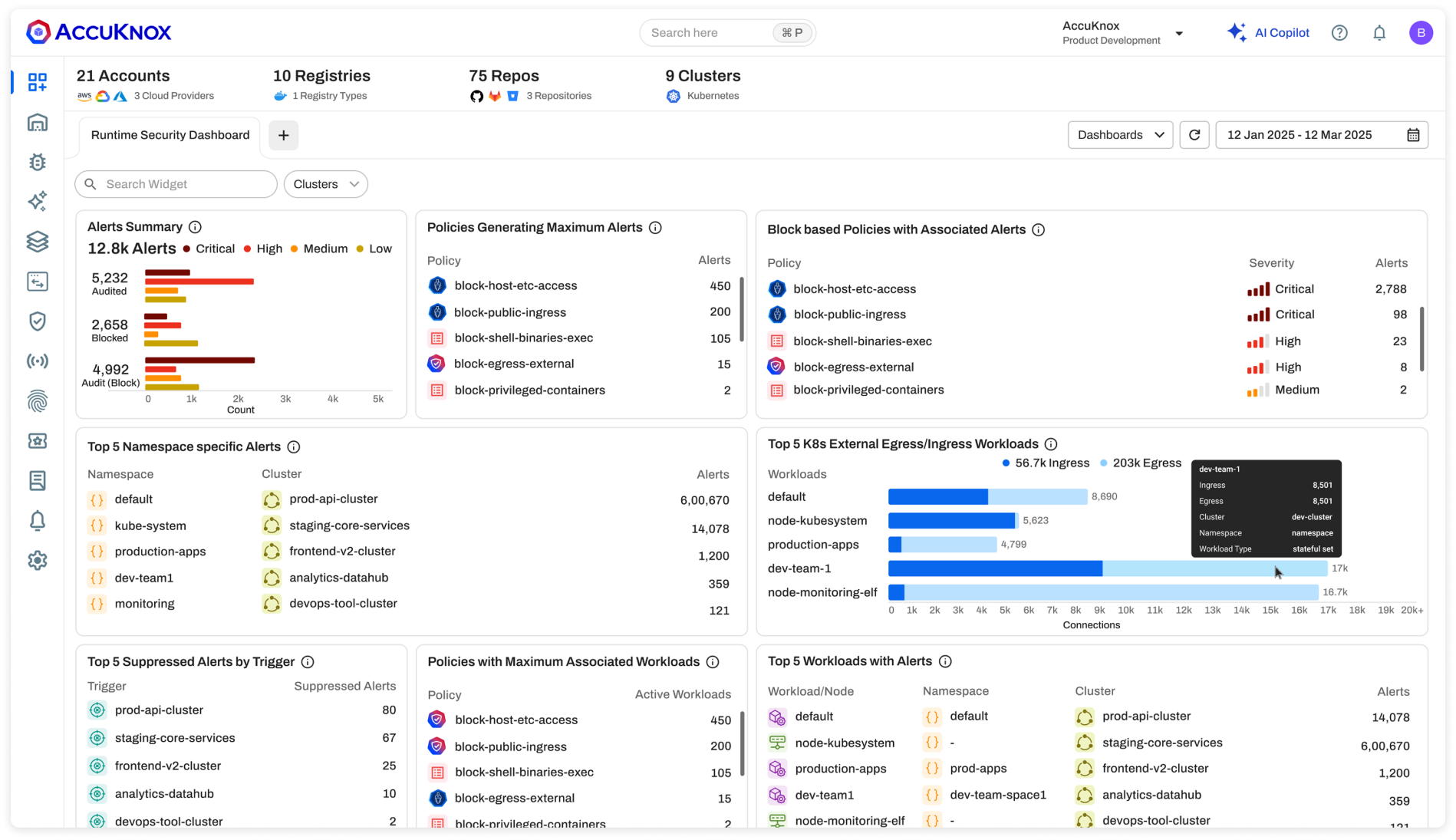
Cloud Security (CSPM / CWPP / KSPM)
Detects misconfigurations, enforces compliance, and protects workloads in cloud and Kubernetes clusters.
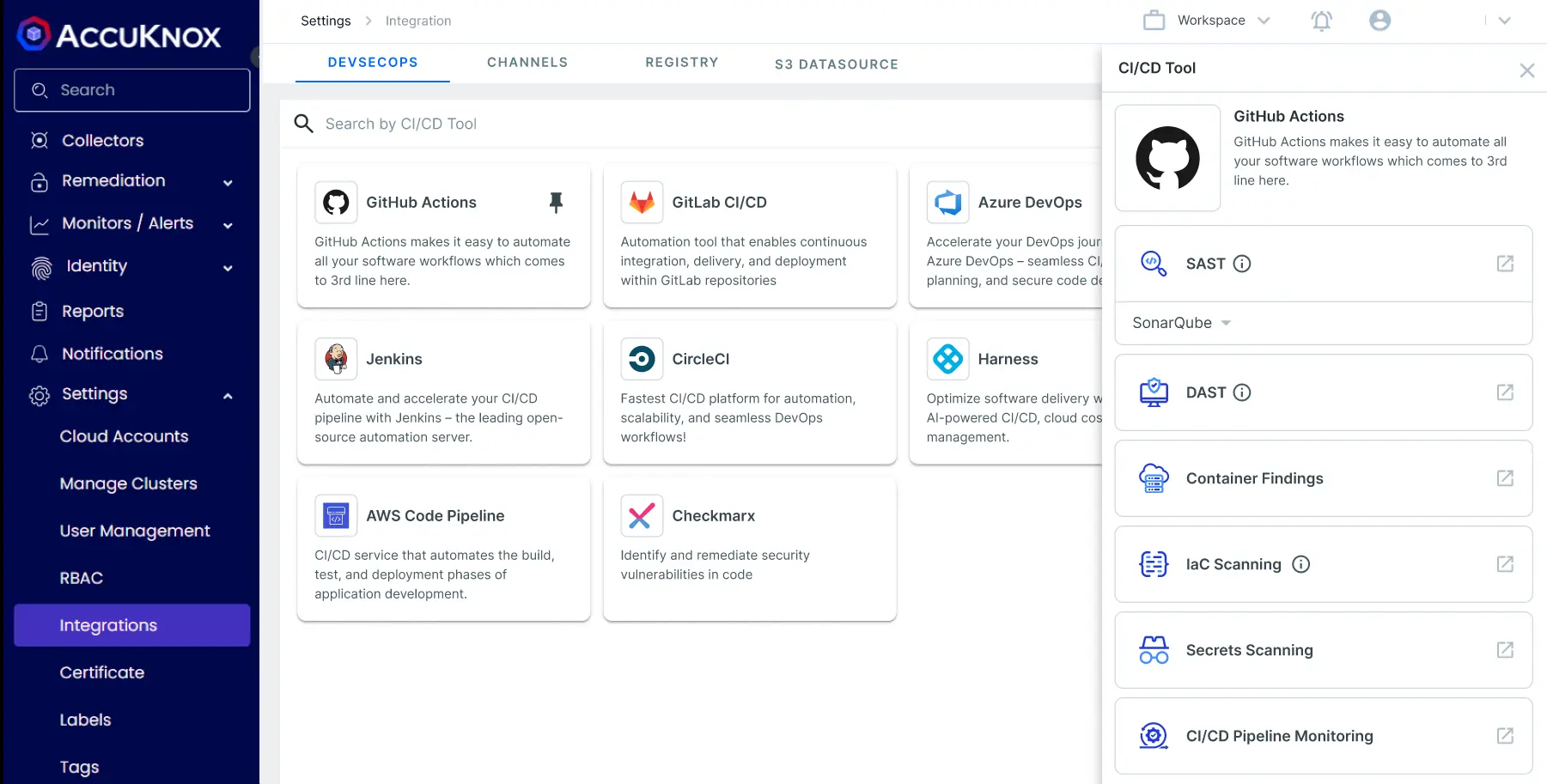
Application Security (ASPM)
Integrates into CI/CD pipelines with SAST, DAST, SCA, and secret-scanning to secure code before deployment.
API & Identity Security
Provides complete visibility into API traffic, prevents data leaks, and secures credentials and secrets.
AI / Edge / IoT Protection
Extends Zero Trust to AI infrastructure and connected edge or IoT environments.
Trusted by Leading Companies







Use Cases & News
Challenge: AI and IoT infrastructures introduce unique attack surfaces — from exposed APIs and model theft to compromised edge devices and data leakage. Securing distributed workloads at scale while maintaining…
Challenge: Fast-moving development teams often release code before security validation, leaving vulnerabilities, secrets, and misconfigurations exposed in production. Traditional tools either slow development or fail to integrate smoothly into existing…
Challenge: Modern enterprises operate across multiple cloud providers — AWS, Azure, GCP — and deploy workloads in containerized or Kubernetes environments. This creates fragmented visibility, inconsistent policy enforcement, and exposure…