When incidents happen, time is critical. With Censys Search and Censys Enrich, responders can instantly query the entire internet to identify attacker infrastructure, trace malicious activity, and enrich indicators of compromise (IOCs) with detailed context. This intelligence shortens investigation time and improves the accuracy of threat attribution.
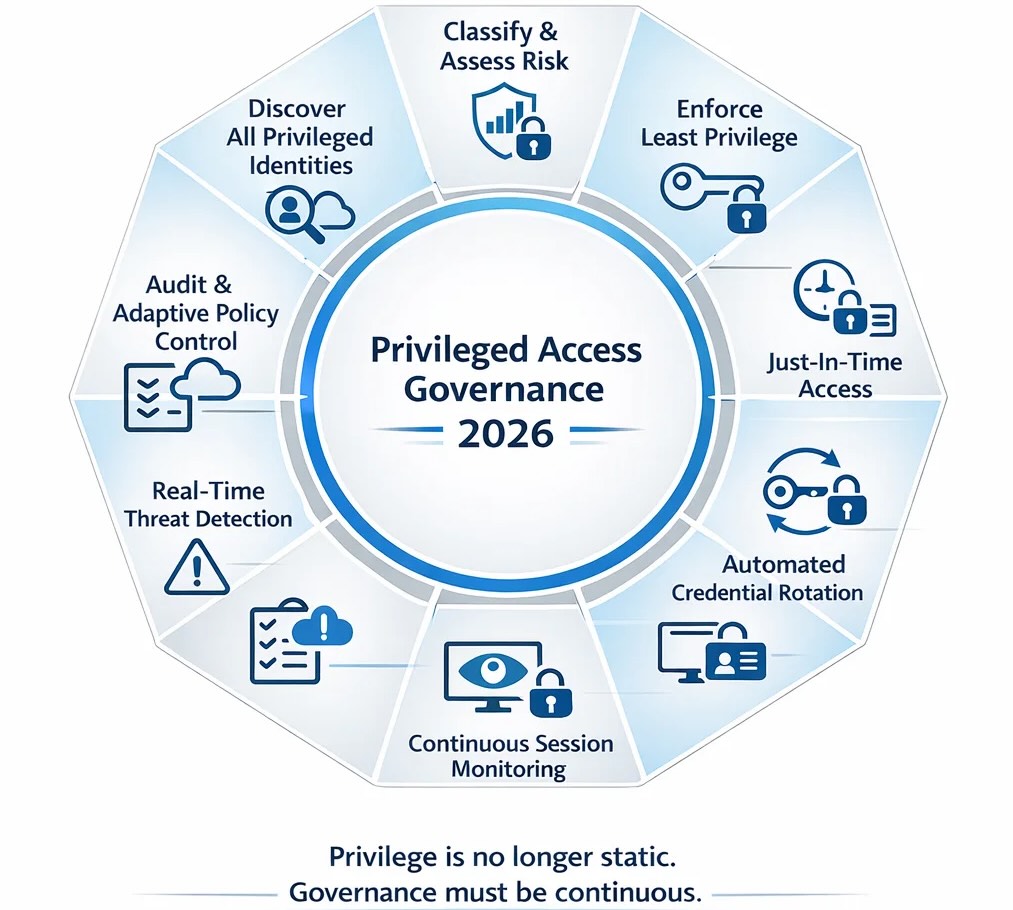
Is Your PAM Strategy Built for 2026?
Privileged Access Management (PAM) is no longer just about vaulting


