For organizations with complex, distributed infrastructure, unknown assets are the biggest blind spot. Censys ASM discovers every internet-facing device, application, and service—whether it’s on-premises, in the cloud, or managed by a third party. This continuous visibility helps security teams eliminate shadow IT, reduce the risk of breach, and ensure compliance across multiple geographies.
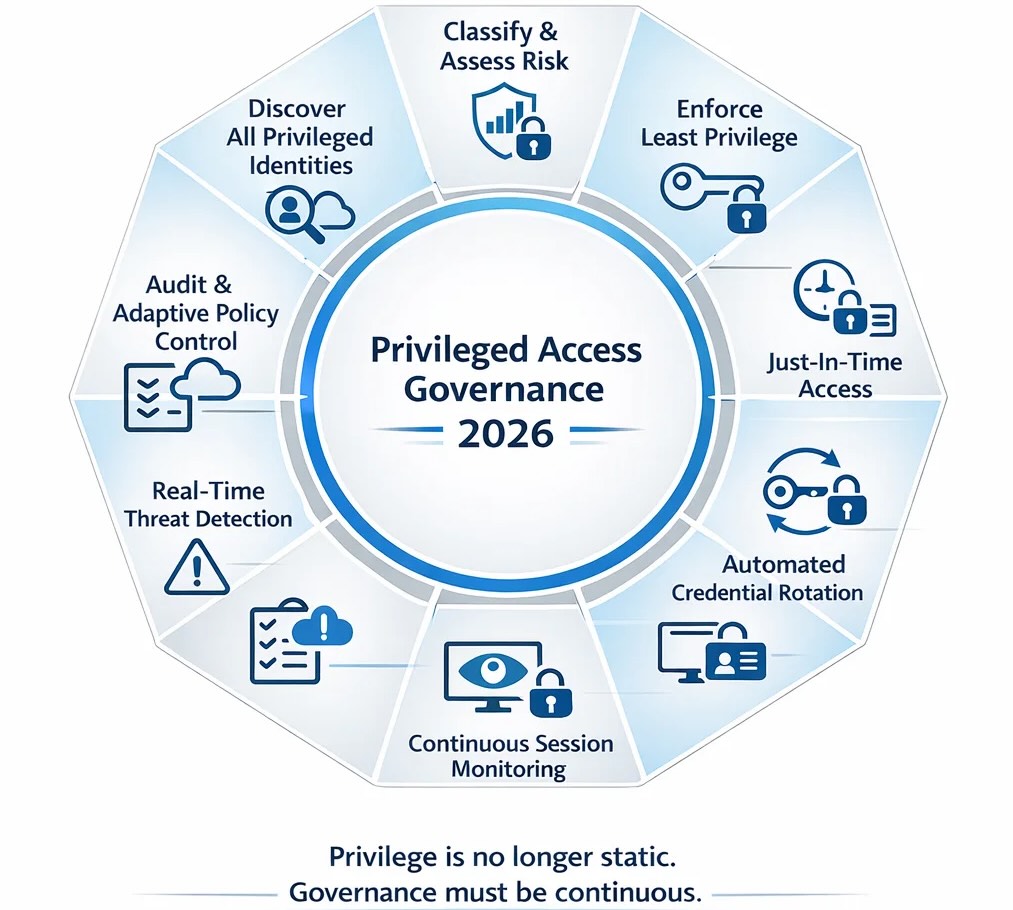
Is Your PAM Strategy Built for 2026?
Privileged Access Management (PAM) is no longer just about vaulting


